We are issuing an important announcement regarding the recent compromise of CurseForge (CF) that has come to our attention. At Minecraft Shader, our primary concern is the safety and security of our users, and we want to ensure that you have the most up-to-date information to protect yourself.
Recently, it has been discovered that a security breach occurred on CurseForge, potentially impacting user accounts and mod downloads. We understand the gravity of this situation and are actively investigating the extent of the breach. Our team is working diligently to address the issue and take necessary measures to secure the platform.
How to know if you are already infected?
- To check for existing infections on your system, follow the steps outlined below:
- Download the detection tool from this location [link to the tool].
- The tool’s GitHub project can be accessed here [link to GitHub project].
- Run the downloaded detection tool on your computer. This tool will scan your system and generate a list of detected files.
- Example output:
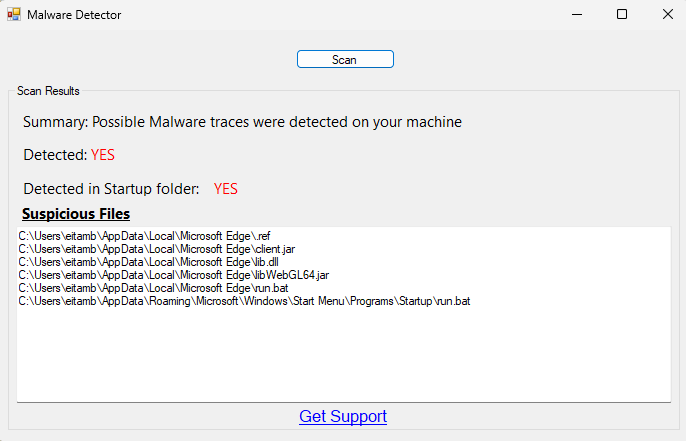
- If the detection tool identifies any infections, please ensure that hidden files are displayed on your system. To do this on Windows, go to the top of your File Explorer window (any opened folder), click on “View,” and then check the “Hidden Items” option.
- Next, manually navigate to each file location mentioned in the detection results and delete those files. Specifically, look for the “Microsoft Edge” folder (with a space in the name) and delete it. Note that the legitimate Edge folder does not have a space in its name.
In addition to these steps, if you were found to be infected, we strongly recommend taking further precautions:
- Run independent malware scanning tools on your system to ensure thorough detection and removal.
- Change important passwords that you have used on your system as an extra safety measure.
To detect any dormant or other infected mods/Jar files, follow the steps below:
- After completing the previous steps, run the Jar Malware Scanning tool. You can access the tool from this link [link to the tool]. The tool’s GitHub page is available here [link to GitHub project].
- Run the Jar Malware Scanning tool even if you were not found infected in the previous step.
- Use the tool to scan all folders that contain Minecraft mod Jars installed on your system.
- Click on “Browse” and select a folder that contains the Jar files, then click on “Scan.”
- This will check the selected folder and its sub-folders for any infected files.
If the scanning tool detects any infected files, a message will be displayed indicating their presence. In such cases, delete the identified Jar file(s) accordingly. Ensure that you cover all folders on your system that contain Mods/Packs for Minecraft.
By following these steps, you can proactively detect and remove any potential infections on your system, ensuring a safer environment for your Minecraft gameplay.

Updated List of Confirmed Infected Mods
List of confirmed mods that were infected but have now been fixed.
- Buried Barrels
- Sky Villages [Forge/Fabric]
- Simply Houses
- When Dungeons Arise -Forge/Fabric
- Skyblock Core
- Prominence [FORGE]
- Medieval MC [FORGE] – MMC3
- Better MC [FORGE] – BMC3
Projects that are infected and taken down permanently:
- Golem Awakening
- Phanerozoic Worlds
- Autobroadcast
- Museum Curator Advanced
- Vault Integrations (Bug Fix) *Note – Not the Modpack Vault Integrations
- AmazingTitles
- dungeonx * Note – Not DungeonZ
- HavenElytra
- DisplayEntityEditor
- The Nexus Event Custom Event
- SimpleHarvesting
- McBounties
- More and Ore advanced
- Easy Custom Foods
- AntiCommandSpam Bungeecord Support
- UltimateLevels
- AntiRedstoneCrash
- hydrationPlugin
- NoVPN
- Fragment Permission Plugin
- Anti ChatReport
- Additional Weapons+
- UVision ENHANCED(server pack only)
- UVision Server(server pack only)
- UVision LITE (server pack only)
- Create: Diesel and Oil Generators
- Ultra Swords Mod
- Simple Frames
- AntiCrashXXL
- Skelegram – The Skript Telegram Addon!
If you have any of the modpacks mentioned above, we strongly advise you to ensure that you have the latest version of the modpack installed. The necessary fixes have been made available, and any infected files have been deleted.
Last Updated: 06/08/2023 09:34 UTC
How to Pootect you CurseForge Account?
In light of this event, we strongly advise all users who have downloaded mods from CurseForge between the dates of [specific date range] to take immediate action. Here are the recommended steps:
- Change your passwords: It is crucial to change your CurseForge account password immediately. Additionally, if you have used the same password for other platforms or services, we recommend changing those passwords as well to maintain account security across all your online activities.
- Run antivirus scans: Perform a thorough scan of your computer or device using reputable antivirus software to detect and remove any potential malware or viruses that may have been downloaded along with the compromised mods.
- Be cautious of suspicious activities: Remain vigilant for any unusual or suspicious activities related to your CurseForge account, such as unauthorized access, unfamiliar changes in settings, or unfamiliar mod downloads. If you notice anything suspicious, report it immediately to the Prism Launcher support team.
- Enable two-factor authentication (2FA): If available, enable two-factor authentication for your CurseForge account. This adds an extra layer of security by requiring a verification code in addition to your password for account access.
Conclusion
Please be assured that we take the security and privacy of our community seriously, and we apologize for any inconvenience caused by this incident. If you have any further questions or require assistance, don’t hesitate to reach out to the appropriate support channels provided by CurseForge.
Thank you for your understanding and cooperation as we work together to maintain a secure environment for the Minecraft community.
Sincerely,
The Minecraft Shader Team






